The digital age has brought unprecedented connectivity and convenience, revolutionizing how we live, work, and communicate. However, this digital transformation has also introduced significant cybersecurity threats. Cyberattacks have become more frequent, sophisticated, and damaging, affecting individuals, businesses, and governments worldwide. It continues to make headlines, underlining the vulnerability of critical infrastructures and large companies in the face of digital threats. Two recent examples illustrate this reality. In September 2023, MGM Resorts International suffered a sophisticated phishing attack, resulting in financial losses of over $100 million and major disruption to its operations. In November 2023, a subsidiary of the Industrial and Commercial Bank of China (ICBC) fell victim to a ransomware attack, disrupting transactions on U.S. Treasury bills and highlighting the growing risks for financial institutions.
The evolving landscape of cyber threats poses substantial risks, necessitating robust cybersecurity measures and significant investments to protect digital assets and ensure the resilience of digital infrastructure. This paper explores the funding challenges, investment opportunities, and sustainability determinants in the cybersecurity sector.
1. Background on Global Cybersecurity
A cyberattack is a malicious attempt to gain access to computer systems, networks or data without authorization. Cyberattacks can take many forms, but one of the most common methods is the ransomware attack, which encrypts victims’ data and demands a ransom for its release. Ransomware attacks can paralyze critical systems and cause significant financial losses, as the incidents involving WannaCry and NotPetya did.
Cybersecurity is “the process of protecting sensitive data from damage or theft.”[1]
In the cybersecurity landscape, we need to distinguish several types of companies.
- The pure cybersecurity companies, also called pure players, retrieve 100% of their revenue from the development of cybersecurity products and services. They are usually startups and leaders in innovation. Some pure players are Palo Alto Networks (USA), CrowdStrike (USA), Fortinet (USA), Darktrace (UK), NCC Group (UK), Stormshield (France), Help AG (United Arab Emirates), DarkMatter (United Arab Emirates), StarLink (United Arab Emirates).
- The IT companies with a branch dedicated to cybersecurity. For example, Airbus in Europe; IBM, Cisco and Microsoft in the U.S.; Saudi Aramco, Etisalat and Saudi Telecom Company through STC Cybersecurity in the GCC.
- The end-users could be called the customers. All the companies and entities from all sectors that are consuming cybersecurity services and products.
2. Investment Trends in Cybersecurity
The cybersecurity sector is a dynamic and rapidly evolving field, driven by the increasing frequency and sophistication of cyber threats. To understand the current landscape and prospects of this sector, it is essential to conduct a SWOT analysis of the sector (2.1), with a particular emphasis on funding challenges (2.2) and the key role played by public-private partnerships (2.3).
2.1. SWOT analysis of the cybersecurity sector
SWOT analysis focuses on strengths, weaknesses, opportunities, and threats.
Strengths
One of the primary strengths of the cybersecurity sector is the growing market demand.
In a world more and more connected (e-commerce platforms, smart devices, cloud solutions, etc.), the exposure to cyber threats has increased, and so has the need for advanced cybersecurity solutions. According to Mordor Intelligence,[2] in 2024 the Cybersecurity Market size is estimated at USD 207.77 billion. By 2029, this market should grow at a CAGR (Compound Annual Growth Rate) of 12.63% and reach USD 376.55 billion.
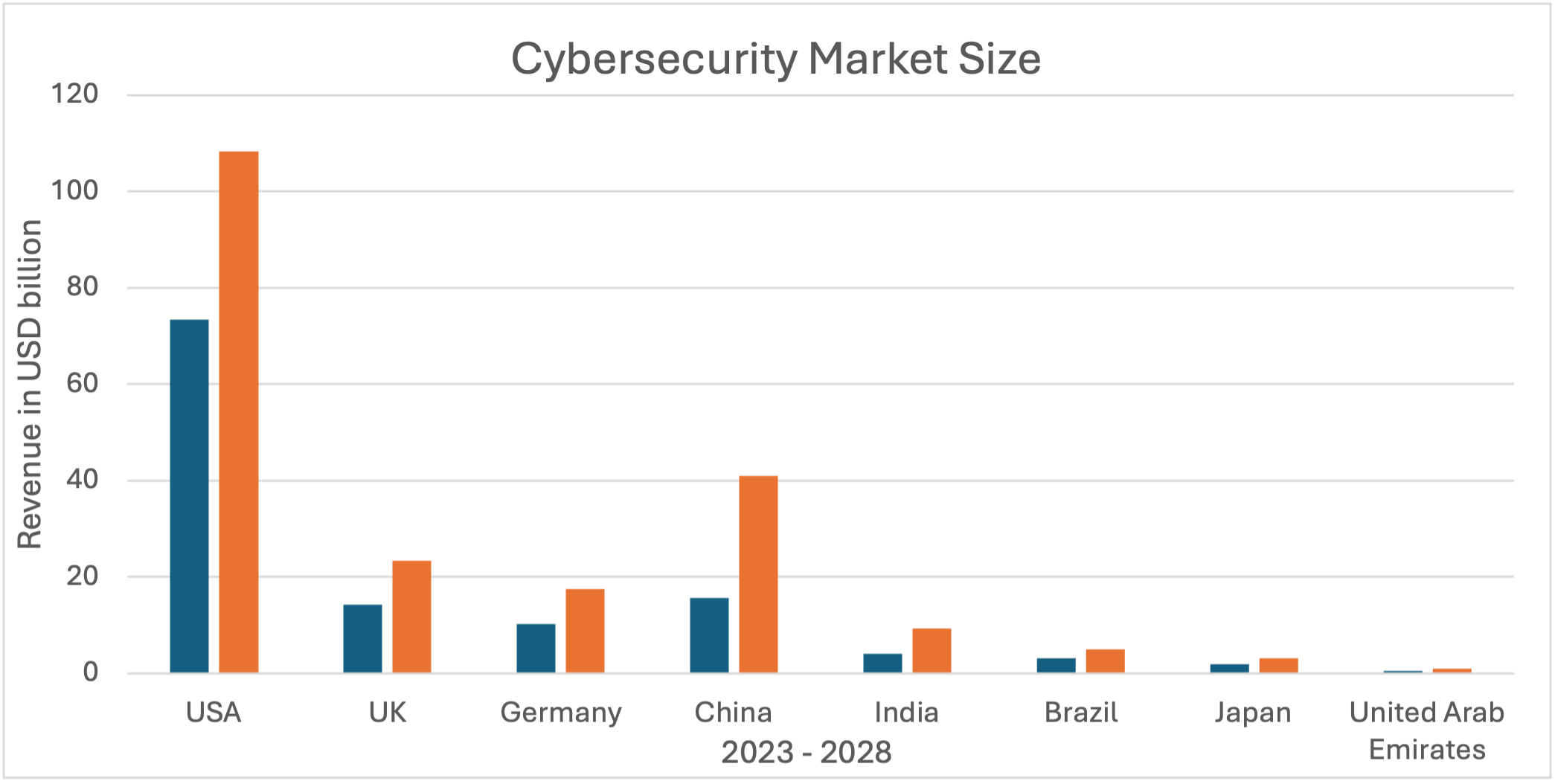
Table 1 below shows the Cybersecurity Market Size, estimated by revenue in USD billion.
| Cybersecurity Market Size | |||
| Revenue in USD billion | |||
| 2023 | 2028 | CAGR (2023-2028) | |
| USA | 73.41 | 108.31 | 8.09% |
| UK | 14.24 | 23.37 | 10.42% |
| Germany | 10.24 | 17.54 | 11.36% |
| China | 15.58 | 40.94 | 21.31% |
| India | 3.97 | 9.21 | 18.33% |
| Brazil | 3.03 | 4.95 | 10.30% |
| Japan | 1.81 | 3.17 | 11.89% |
| United Arab Emirates | 0.52 | 0.95 | 12.72% |
Source: Data retrieved from mordorintelligence.com
Figure 1 below displays the Cybersecurity Market potential growth among several regions in the world.
Source: Data retrieved from mordorintelligence.com
The cybersecurity market is growing overall, and the most impressive growth is located in China and India.
Businesses and governments are investing heavily to protect their digital assets, creating a robust market for cybersecurity products and services. This demand is further bolstered by the increasing digitization of various sectors, from finance to healthcare, which rely on secure digital infrastructure to operate effectively.
Figure 2 below shows global spending in cybersecurity by end-user sector.
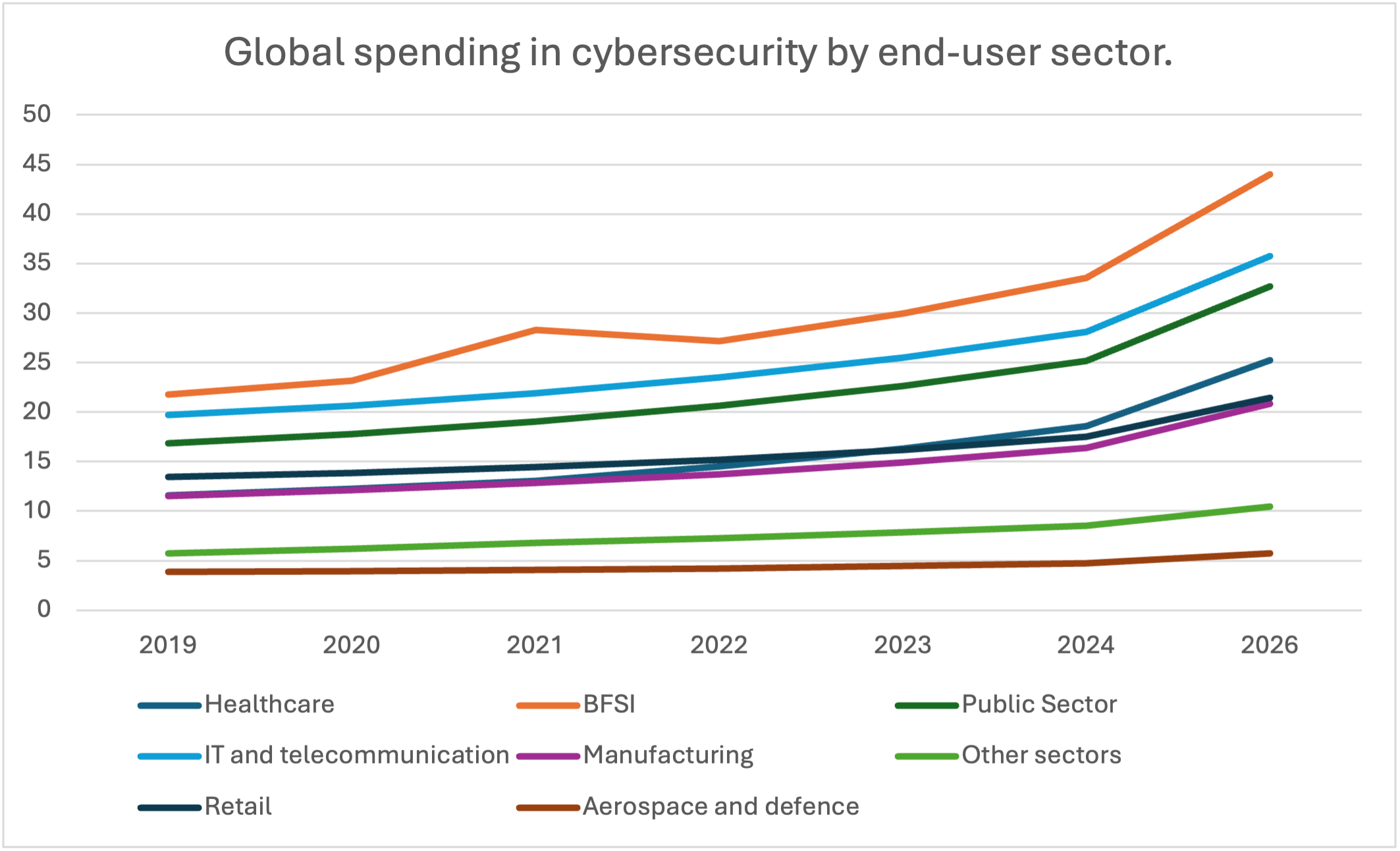
Source: Data retrieved from Mordorintelligence (2021)
Another significant strength is the technological advancements in the field. Innovations in artificial intelligence (AI), machine learning, and blockchain are enhancing the effectiveness of cybersecurity measures. These technologies enable more efficient threat detection and response, allowing organizations to stay ahead of potential threats. For instance, AI can analyze vast amounts of data to identify patterns and anomalies that may indicate a cyberattack, providing a proactive approach to cybersecurity. This point will be developed in section 2.3.
Regulatory support also plays a crucial role in strengthening the cybersecurity sector. Indeed, regulations mandate robust cybersecurity practices, creating a stable market for cybersecurity products and services. Governments worldwide are implementing stringent data protection regulations.
- In the European Union, the General Data Protection Regulation (GDPR)[3] came into effect on 25 May 2018. This comprehensive data privacy law aims to protect individuals’ privacy rights by granting them control over their personal data.
- In the U.S., the California Consumer Privacy Act (CCPA),[4] effective 1 January 2020, enhances privacy rights for California residents. It grants consumers the right to know what personal information is collected about them, request its deletion, and opt out of its sale.
- In recent years, several Gulf countries have implemented comprehensive data protection regulations to safeguard personal information and enhance cybersecurity. The United Arab Emirates introduced the Federal Decree-Law No. 45 of 2021,[5] which mandates robust security measures and grants individuals’ rights over their personal data. Similarly, Saudi Arabia’s Personal Data Protection Law (PDPL),[6] effective from March 2022, imposes strict obligations on businesses to protect personal data and ensures individuals’ rights to access and correct their information. Qatar’s Law No. 13 of 2016[7] on Personal Data Protection also sets stringent requirements for data handling and security, reflecting a growing commitment across the region to align with global standards like the GDPR. These regulations collectively signify a significant step toward enhancing data privacy and cybersecurity in the Gulf.
Those kinds of regulations encourage companies to adopt rigorous cybersecurity practices to protect personal data, thereby reducing the risk of cyberattacks and data breaches.
Weaknesses
Despite its strengths, the cybersecurity sector faces several weaknesses, one of which is the high costs associated with developing and maintaining advanced cybersecurity infrastructure. The estimated cost of cybercrime in the global cybersecurity market is expected to increase continuously between 2024 and 2029, reaching a total of $6.4 trillion (+69.41%). After the eleventh consecutive year of increase, it is estimated that the indicator will reach $15.63 trillion, setting a new record in 2029. Notably, the ‘Estimated Cost of Cybercrime’ indicator in the cybersecurity market has continuously increased over the past few years.[8]
Figure 3 below displays the estimated average cost of Cybercrime.
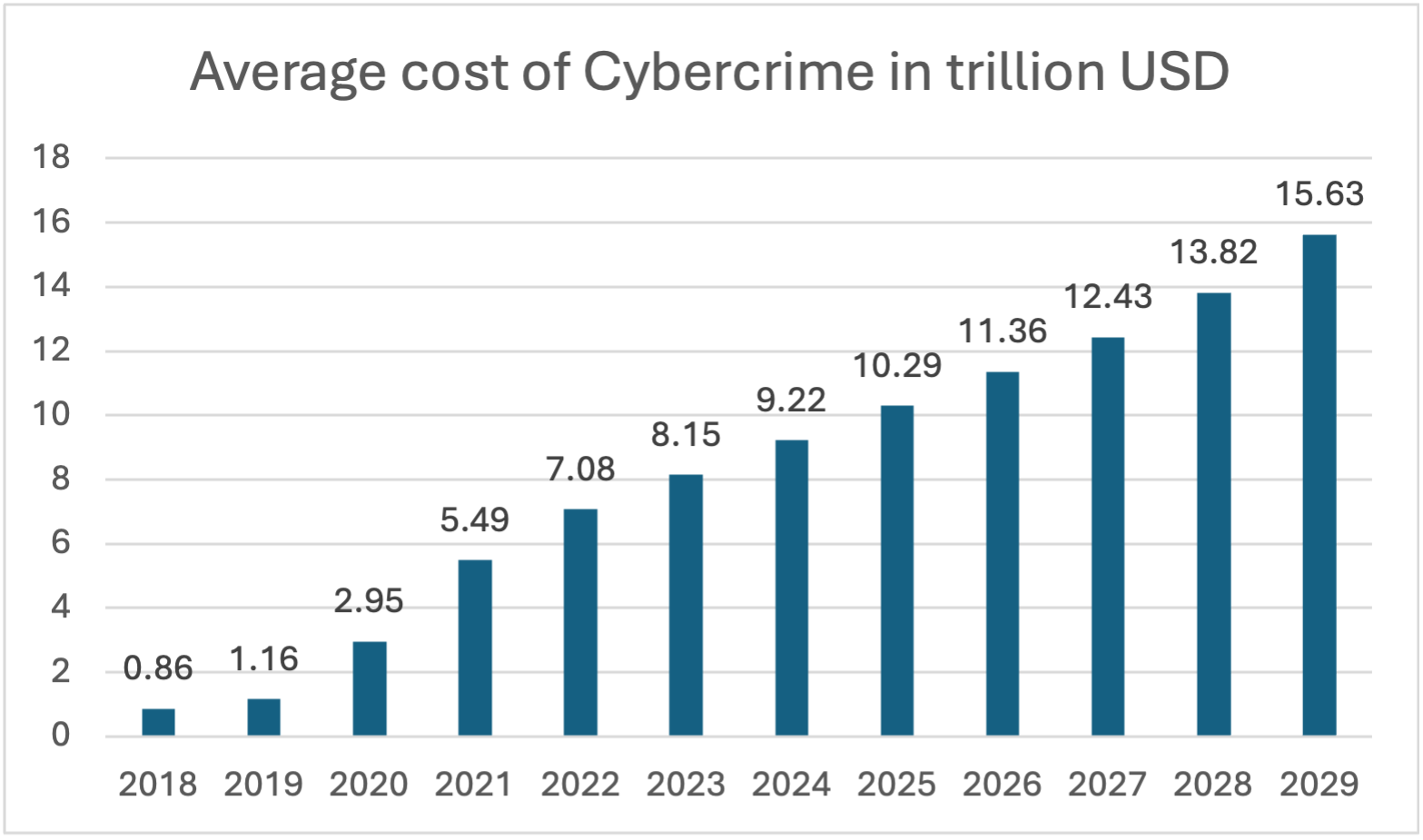
Source: Statista (2024) based on a survey between 2018 and 2019 in Australia, Brazil, Germany, Japan, Russia, UK, USA.
Among all companies, Small and medium-sized enterprises (SMEs) often struggle to afford comprehensive cybersecurity solutions, leaving them vulnerable to attacks. The high barrier to entry can prevent smaller organizations from adopting necessary protections, increasing the overall risk landscape. Yet, according to the European Alliance Digital SME report,[9] SMEs face a growing threat from ransomware attacks, jeopardizing the security of their data and business operations. Furthermore, SMEs with a smaller workforce are the most affected. Specifically, companies with a staff size ranging from 1 to 50 employees constitute the most affected group.
The rapidly evolving threat landscape is another challenge for the cybersecurity sector. Cyber threats are constantly evolving, making it challenging to stay ahead. This dynamic environment requires continuous investment in research and development, which can strain resources. Organizations must stay vigilant and adaptable to address new and emerging threats effectively.
Another critical weakness is the talent shortage in the cybersecurity field. There is a significant gap between the demand for skilled cybersecurity professionals and the available workforce. According to the ISC2 Cybersecurity Workforce Study 2024,[10] there is a global need for 4.8 million cybersecurity professionals to effectively secure organizations, representing a 19% increase from the previous year. The study also highlights that 90% of organizations face skill shortages, putting their security at risk. World Economic Forum explains that the situation is even worse within SMEs: “Half of the smallest organizations by revenue say they either do not have or are unsure as to whether they have the skills they need to meet their cyber objectives.”[11]
- In the U.S., the National Initiative for Cybersecurity Education (NICE) by GAO,[12] establishes that there is a shortfall of almost 448,033 cybersecurity professionals as of January 2024. Furthermore, “From September 2023 through August 2024, there were only 83 cybersecurity workers available for every 100 cybersecurity jobs demanded by employers.”[13]
- In the Gulf countries, the growth of the cybersecurity workforce has been notable. For instance, the same ISC2 study indicates a 7.4% increase in the cybersecurity workforce in the Middle East and Africa in 2024. However, despite this growth, the region continues to face significant challenges in addressing the cybersecurity talent shortage, exacerbated by geopolitical tensions and economic constraints.
This talent gap makes it difficult for organizations to build effective cybersecurity teams and can lead to increased costs for hiring and training. The shortage of skilled professionals also means that existing teams are often overburdened, which can impact the quality of cybersecurity measures.
Opportunities
The cybersecurity sector also presents numerous opportunities, particularly with the increasing use of cloud computing and connected objects (Internet of Things – IoT) creating new opportunities for cybersecurity solutions. “With the ubiquity of the Internet of Things (IoT), the explosion in network connectivity, and many associated applications, cybersecurity has become a focal point of contemporary security concerns.”[14]
According to Kaspersky,[15] the rise of edge computing has shifted from centralized to decentralized computing. This change is driven by the IoT, with many devices like smartphones and home appliances connected to the internet. As a result, more computing and storage will happen at the edges of the internet, closer to where data is generated. This increase in endpoints also expands the threat landscape, creating more potential vulnerabilities for cyberattacks, thus necessitating enhanced cybersecurity solutions.
Expansion into emerging markets is another significant opportunity for the cybersecurity sector (See Brazil and India in Table 1). As developing countries continue to digitize, there is a growing need for cybersecurity solutions. Companies that can tap into these emerging markets stand to gain substantial growth opportunities. Providing affordable and scalable cybersecurity solutions to these markets can help bridge the digital divide and enhance global cybersecurity resilience.
Increased public-private partnerships also offer opportunities for advancing cybersecurity. Collaboration between governments and private companies can lead to the development of more robust cybersecurity frameworks. These partnerships can provide funding and resources for cybersecurity initiatives, fostering innovation and enhancing security measures. Successful examples include the European Union’s Horizon 2020 program and the United States Cybersecurity and Infrastructure Security Agency (CISA). This point will be developed in section 2.2.
Threats
One of the main threats in the cybersecurity sector is the sophistication of cyberattacks, such as state-sponsored attacks and advanced persistent threats (APTs). “Advanced persistent threats (APTs) are undetectable cyberattacks designed to steal sensitive data, conduct cyberespionage or sabotage critical systems over a long period of time. Unlike other cyberthreats such as ransomware, the aim of an APT attack group is to remain undetected while infiltrating and extending its presence within a target network.”[16] According to Kaspersky,[17] APTs are expected to become more sophisticated and targeted in 2024. They predict an increase in the use of AI and machine learning by attackers to enhance their capabilities. Additionally, there will be a focus on exploiting vulnerabilities in mobile devices, wearables, and smart home technologies.[18]
The report also mentions that geopolitical tensions will likely drive more state-sponsored APT activities, with attackers using advanced techniques to remain undetected for longer periods. Moreover, tensions between countries can lead to an increase in cyber espionage and cyber warfare, complicating the cybersecurity environment.
Further, the significant growth in the sector is likely to attract new entrants, intensifying competition within the industry. Such increased competition poses a threat as it can lead to price wars, reduced profit margins, and the need for continuous innovation to maintain market share. Established companies may find it challenging to differentiate themselves, especially if new players introduce disruptive technologies or more cost-effective solutions.
Table 2 below summarizes the SWOT analysis of the Cybersecurity sector.
| SWOT analysis of Cybersecurity Sector | |
| Strengths | Weaknesses |
| Growing market demand | High costs |
| Technological advancements | Rapidly evolving threat landscape |
| Regulatory support | Talent shortage |
| Opportunities | Threats |
| Cloud computing & IoT | Sophistication |
| Emerging markets | Geopolitical tensions |
| Public-Private Partnerships (PPPs) | Competition |
Source: Authors
2.2. Funding challenges and the role of public-private partnerships (PPPs)
One of the primary funding challenges in the cybersecurity sector is the high initial investment required to implement comprehensive cybersecurity measures. This high cost can be prohibitive, especially for SMEs (as highlighted before in the paper), preventing them from adopting necessary protections. According to the World Economic Forum,[19] the number of organizations that maintain minimum viable cyber resilience has decreased by 30%, with SMEs being disproportionately affected. Addressing this challenge requires innovative funding models and government incentives to make cybersecurity solutions more accessible.
Sustained funding needs are another challenge. Cybersecurity is not a one-time investment; it requires ongoing funding for maintenance, updates, and training. Organizations must continuously allocate resources to stay ahead of evolving threats.
Moreover, measuring the Return on Investment (ROI) of cybersecurity investments can be difficult, as the benefits are often intangible and preventative. Unlike other business investments, the value of cybersecurity is in preventing potential losses rather than generating direct revenue. This makes it challenging to justify the expenditure to stakeholders.
Also, cybersecurity must compete with other critical areas within organizations for funding, which can lead to underinvestment.
Finally, access to capital is a challenge for startups and smaller cybersecurity firms. The high-risk nature of the cybersecurity sector can deter investment, limiting the growth and innovation potential of these companies. Addressing this challenge requires creating a supportive investment environment.
One promising approach is the development of public-private partnerships (PPPs). These partnerships can leverage government support and private-sector innovation to provide the necessary funding and resources. According to the World Economic Forum, PPPs are essential for effective cybersecurity investment. By leveraging the strengths of both sectors, these collaborations drive innovation, enhance resource allocation and address funding challenges.
- Programs like the EU’s Horizon 2020[20] have funded numerous cybersecurity projects, driving technological advancements.
- The European Cybersecurity Investment Platform (ECIP)[21] is another initiative aiming at addressing the funding gap in the cybersecurity sector across Europe. Launched in collaboration with private investors and the European Commission, this platform plans to invest at least 1 billion euros over five years. The main goals of the ECIP include promoting investments in European cybersecurity start-ups and SMEs, fostering the emergence of specialized cybersecurity funds at the European level, and supporting growth-phase companies to provide them with fair conditions. This initiative is crucial for strengthening cybersecurity capabilities in Europe and ensuring that strategic skills and solutions remain within the continent.
PPPs also strengthen national security and facilitate information sharing. Governments rely on private sector expertise to protect critical infrastructure, such as power grids, financial systems, and communication networks, from cyberattacks. In return, private companies benefit from government support in the form of intelligence sharing, regulatory frameworks, and financial incentives. This collaboration enhances the overall security posture of a nation, making it more resilient to cyber threats.
- The United States Cybersecurity and Infrastructure Security Agency (CISA)[22] exemplifies this approach.
- The National Cybersecurity Authority (NCA) in Saudi Arabia could be another interesting example. NCA is not a public-private partnership (PPP) itself, but it does engage in significant collaboration with the private sector. The NCA, responsible for enhancing the cybersecurity posture of Saudi Arabia, works closely with private companies to enhance the cybersecurity landscape in the country.
3. AI Boom and Its Impact on Future Trends in Cybersecurity
Is the cybersecurity sector becoming more attractive to investors following advancements in AI?
“AI delineated by pioneers such as John McCarthy in 1956, refers to the science and engineering of making intelligent machines.”[23]AI has been introduced in many sectors, including the cybersecurity sector, where it has brought considerable changes. For example, AI has been critical in building automated security systems, face detection, natural language processing, automatic threat detection and better new attack prediction (Mordor Intelligence[24]). “AI technology has ensured faster detection of malfunctioning in the system as their monitoring stills are much greater than those of man.”[25]
Researchers[26] studied how we can use AI, including machine learning (ML) and deep learning (DL), alongside metaheuristic algorithms to detect cyberattacks better. “The first key of attribute of AI being significantly embedded in systems is learning from their experiences.”[27]
Because of all the possibilities and advances offered by AI, we can observe a “hype” around it, which refers to widespread excitement and enthusiasm for it. This is reflected in intense media coverage, increased investment by companies in the sector, and high expectations for the future capabilities of AI and its potential impact on various sectors. The “hype” around AI has also benefited other companies. Investors are enthusiastic about all AI-related stocks. For example, Vistra (VST), an electricity producer, registered the highest increase among S&P 500 boosted by optimistic forecasts for AI-related energy consumption.[28]
Many sectors benefit from AI advances, but none like the cybersecurity sector, which makes it attractive to investors. Overall, the combination of technological advancements, market demand (see 3.1), and strategic importance makes the cybersecurity sector a compelling investment opportunity.
4. Strengthening the Sustainability of Cybersecurity Investment Funding
4.1. Key incentives for investment
As highlighted before in the opportunities of the SWOT analysis, the cybersecurity sector is a highly promising sector that should attract the attention of investors.
First of all, spending on cybersecurity makes it a sector of high demand and high potential growth. According to the European Investment Bank,[29] global cybersecurity spending in Europe is about 0.1% of GDP, but in the U.S., it is around 0.35%. The U.S. federal government supported cybersecurity companies with approximately €15 billion in 2019 and €16.7 billion in 2021, including nearly €800 million for research and innovation. China has a €9 billion program focused on quantum technologies for cybersecurity. In contrast, the EU’s public spending on cybersecurity is lower, fragmented, and lacks coordinated strategies, estimated to be between €1 billion and €2 billion annually. Some EU member states spend as little as one-tenth of the U.S. levels proportionally. Germany and France lead the EU cybersecurity market, followed by Italy, Spain, Poland, and the Netherlands. Before Brexit, the UK was the largest EU cybersecurity actor in terms of investment and company numbers. The analysis separates the UK from the EU to highlight its significant role in the market.
Second, companies of the sector and investment funds show interesting price evolution. Figure 4 shows some famous funds dedicated to the sector, such as iShares Digital Security (LOCK.L), L&G Cyber Security (ISPY.L), Globalx cybersecurity (BUGG.AX) and First Trust Nasdaq Cybersecurity (CIBR.O). We can observe that their evolution is above S&P 500 (SPX).
Figure 4 below illustrates price evolution of investment funds dedicated to cybersecurity sector.
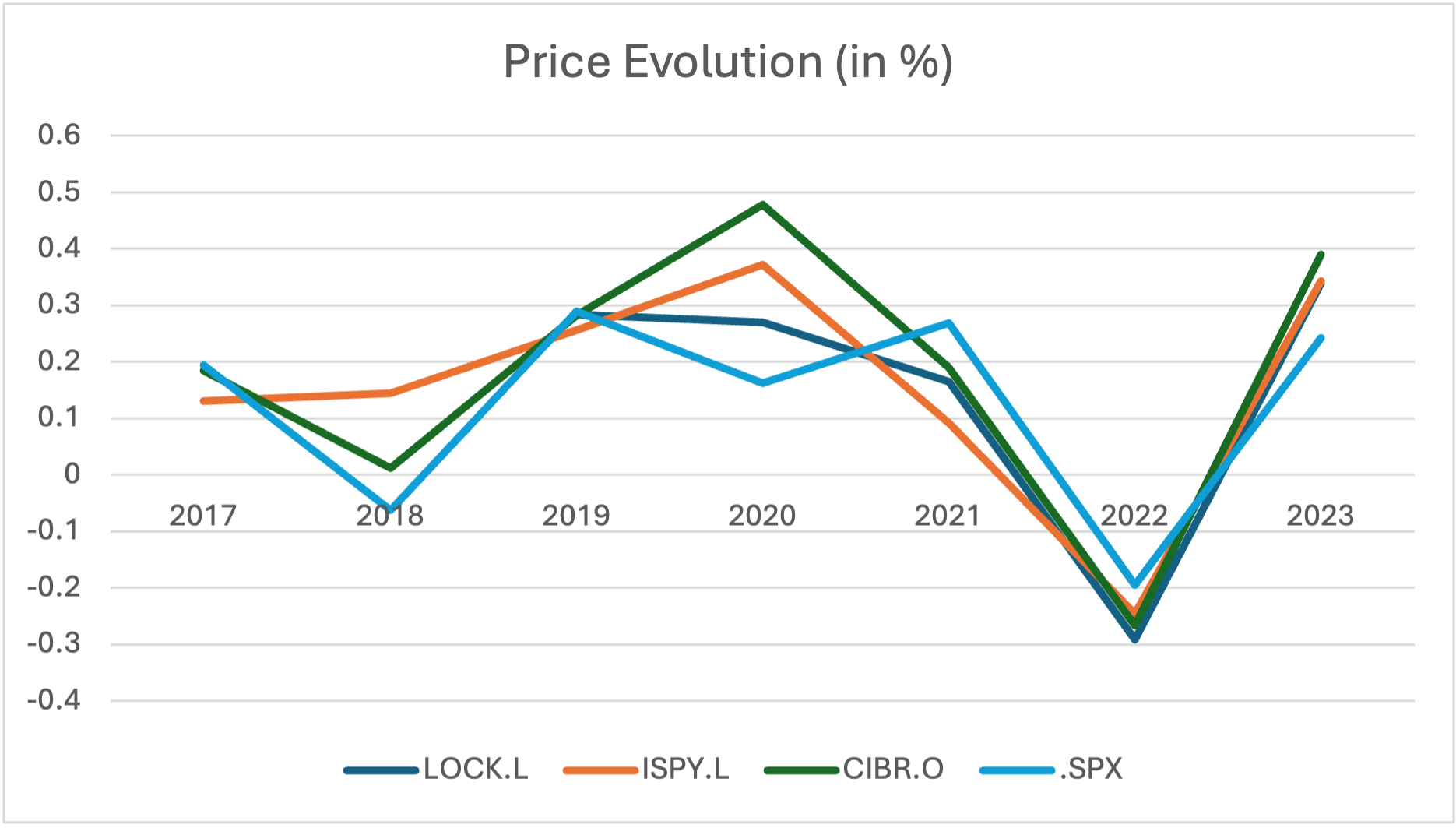
Source: Data retrieved from Refinitiv
Figure 5 below displays the price evolution of pure players like Palo Alto Networks (PANW.O), CrowdStrike (CRWD.O), Fortinet (FTNT.O) and Darktrace (DRKTY.PK). On average, they all overperform S&P 500 (SPX).
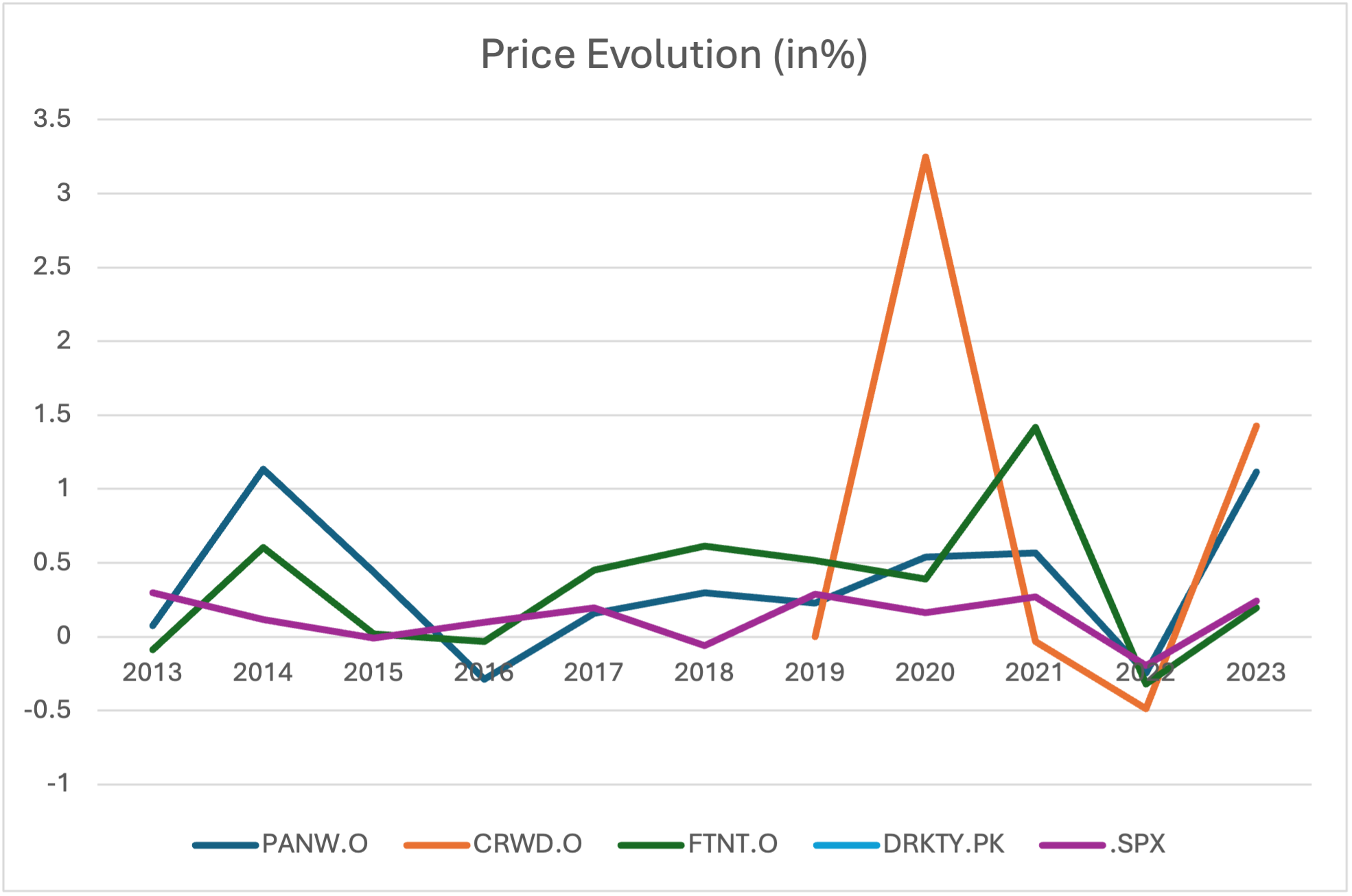
Source: Data retrieved from Refinitiv
Finally, most of the big companies in the sector show an appealing Price-to-Book ratio (P/B). This financial indicator compares a company’s market value to its book value. It is calculated by dividing the current stock price by the book value per share. The average price to book of those 15 companies is 9.25. As a reminder, it means that the market values the company at 9 times its book value. This can indicate that investors expect very high future growth or that the company has intangible assets (such as patents or a strong brand) that are not reflected in the book value.
Table 3 below shows the 15 biggest companies of the sector, based on their market capitalization in USD.
| Identifier (RIC) | Company Name | Market Cap (USD) | Price To Book | Beta 5 Year |
| Summary (15) | 17,978,127,492.09 | 9.25 | 1.09 | |
| PANW.OQ | Palo Alto Networks Inc | 125,780,416,000 | 21.25 | 1.12 |
| FTNT.OQ | Fortinet Inc | 71,103,816,793 | 78.22 | 0.99 |
| CHKP.OQ | Check Point Software Technologies Ltd | 19,989,321,011 | 7.07 | 0.63 |
| GEN.OQ | Gen Digital Inc | 18,603,228,044 | 8.86 | 0.75 |
| CYBR.OQ | Cyberark Software Ltd | 13,821,704,728 | 10.99 | 1.13 |
| RBRK.N | Rubrik Inc | 9,273,396,422 | -18.55 | Nd |
| 300454.SZ | Sangfor Technologies Inc | 3,657,463,519 | 3.19 | 1.51 |
| 300768.SZ | Hangzhou DPtech Technologies Co Ltd | 1,645,870,719 | 3.72 | 1.15 |
| BB.TO | BlackBerry Ltd | 1,391,191,916 | 1.90 | 1.06 |
| 688225.SS | Asiainfo Security Technologies Co Ltd | 1,188,400,260 | 4.24 | Nd |
| RDWR.OQ | Radware Ltd | 973,022,273 | 3.18 | 0.97 |
| OSPN.OQ | OneSpan Inc | 679,280,081 | 3.48 | 0.76 |
| CGNT.OQ | Cognyte Software Ltd | 562,218,658 | 2.86 | 1.77 |
| 2326.T | Digital Arts Inc | 547,904,149 | 4.99 | 1.28 |
| 688651.SS | WebRAY Tech Beijing Co Ltd | 454,677,808 | 3.38 | Nd |
Source: Data retrieved from Refinitiv
Investors should also pay attention to the Beta which is a measure of its volatility relative to the overall market. It indicates how much the price of a stock fluctuates in comparison to a benchmark index, such as the S&P 500. For example, a beta of 1.5 means that if the market goes up by 1%, the stock will go up by 1.5%. This indicates higher risk but also higher potential returns.
4.2. Expected roles of sovereign wealth funds
Several governments recognize the importance of cybersecurity in protecting their investments and supporting technological innovation through sovereign funds. As a reminder, a sovereign wealth fund (SWF) is a state-owned investment fund composed of financial assets such as stocks, bonds, real estate, or other financial instruments. These funds are typically established from the balance of payments surpluses, official foreign currency operations, the proceeds of privatizations, fiscal surpluses, and/or receipts resulting from commodity exports.[30]
For example, we can point out the Public Investment Fund (PIF) in Saudi Arabia, the Abu Dhabi Investment Authority (ADIA), the Norway Government Pension Fund Global, the Ireland Strategic Investment Fund, the Alaska Permanent Fund, the Texas Permanent School Fund, the China Investment Corporation, GIC Private Limited.
They play a crucial role in providing the capital needed to develop advanced cybersecurity solutions. Their involvement not only ensures sustained funding but also signals the strategic importance of cybersecurity to national security and economic stability. This governmental support is complemented by a growing recognition among private investors of the sector’s potential. The stock market performance of cybersecurity firms and dedicated investment funds reflects this awareness, with many investors keenly eyeing the sector’s promising future.
Conclusion
The cybersecurity sector is experiencing significant growth, driven largely by advancements in artificial intelligence (AI). This rapid evolution underscores the critical importance of robust cybersecurity measures in an increasingly digital world. Governments worldwide have recognized this necessity and are actively supporting the sector’s development through public-private partnerships and sovereign wealth funds. These initiatives are crucial, as continuous investment is essential to keep pace with the ever-evolving landscape of cyber threats. The combined efforts of public and private entities are essential to address the funding challenges and seize investment opportunities within this dynamic field.
Keeping a close watch on developments of the sector will be crucial for stakeholders aiming to navigate and thrive in the digital age.
[1] Taherdoost, H., “Understanding Cybersecurity Frameworks and Information Security Standard – A review and Comprehensive overview,” Electronics, 11, 2181 (2022).
[2] “Cyber Security Market Size, Share, Trends & Industry Growth (2025-2030), Mordor Intelligence, https://www.mordorintelligence.com/industry-reports/cyber-security-market.
[3] European Union, “General Data Protection Regulation,” 2016, https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A32016R0679. (accessed on November 12, 2024).
[4] California Department of Justice, “California Consumer Privacy Act (CCPA),” https://www.oag.ca.gov/privacy/ccpa. (accessed on November 12, 2024).
[5] UAE, “Federal Decree Law No. 45 of 2021 Regarding the Protection of Personal Data,” 2021, https://u.ae/en/about-the-uae/digital-uae/data/data-protection-laws. (accessed on November 12, 2024).
[6] Saudi Data & IA security, “Personal Data Protection Law,” 2021, https://sdaia.gov.sa/en/SDAIA/about/Documents/Personal%20Data%20English%20V2-23April2023-%20Reviewed-.pdf. (accessed on November 12, 2024).
[7] NCSA, “Law No.13 of 2016 Personal Data Privacy Protection,” available at Law No.13 of 2016 (accessed on November 12, 2024).
[8] Statista, 2024, https://fr.statista.com/statistiques/573396/cybercriminalite-perte-moyenne-des-entreprises-dans-une-selection-de-pays/. (accessed on November 8 , 2024).
[9] European Alliance Digital SME, “The Ransomware Landscape in Europe,” Swascan, 2023, Report-H1-Europa-ENG.pdf. (accessed on November 8, 2024).
[10] “Growth of Cybersecurity Workforce Slows in 2024 as Economic Uncertainty Persists,” ISC2, September 11, 2024, https://www.isc2.org/Insights/2024/09/ISC2-Publishes-2024-Cybersecurity-Workforce-Study-First-Look.
[11] World Economic Forum, “Global Cybersecurity Outlook 2024,” 2024, https://www3.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2024.pdf. (accessed on November 13, 2024).
[12] “National Initiative for Cybersecurity Education,” GAO, 2023, GAO-23-105945, CYBERSECURITY WORKFORCE: National Initiative Needs to Better Assess Its Performance (accessed on November 12th, 2024).
[13] Cyber Seek, https://www.cyberseek.org/.
[14] Salem, A. H., Azzam, S. M., Emam, O. E., and Abohany, A. A., “Advancing cybersecurity: a comprehensive review of AI‑driven detection techniques,” Journal of Big Data 11 (2024): https://doi.org/10.1186/s40537-024-00957-y.
[15] “What does the rise of edge computing mean for cybersecurity?” Kaspersky, 2019, https://www.kaspersky.com/blog/secure-futuresmagazine/. edge-computing-cybersecurity/31935/, (accessed on November 12th , 2024).
[16] IBM, 2024, https://www.ibm.com/fr-fr/topics/advanced-persistent-threats.
[17] “Ahead of the Curve: Kaspersky’s projections for 2024’s Advanced Threats Landscape,” Kaspersky, November 14, 2023, https://www.kaspersky.com/about/press-releases/ahead-of-the-curve-kasperskys-projections-for-2024s-advanced-threats-landscape. (accessed on November 12, 2024).
[18] Ibid.
[19] World Economic Forum, “Global Cybersecurity Outlook 2024.”
[20] “Horizon 2020,” European Commission, https://research-and-innovation.ec.europa.eu/funding/funding-opportunities/funding-programmes-and-open-calls/horizon-2020_en.
[21] “European Cybersecurity Investment Platform,” ECSO, https://ecs-org.eu/activities/european-cybersecurity-investment-platform/
[22] CISA, https://www.cisa.gov/.
[23] Salem et al., “Advancing cybersecurity: a comprehensive review of AI‑driven detection techniques.”
[24] “Cyber Security Market Size, Share, Trends & Industry Growth (2025-2030).”
[25] Ansari, M.F. et al., “The Impact and Limitations of Artificial Intelligence in Cybersecurity: A Literature Review,” IJARCCE 11, no. 9 (2022): p. 83.
[26] See Salem et al., “Advancing cybersecurity: a comprehensive review of AI‑driven detection techniques.”
[27] Ansari, M.F. et al., “The Impact and Limitations of Artificial Intelligence in Cybersecurity: A Literature Review.”
[28] L’Echo, November 13, 2024, Qui seront les prochains gagnants de l’IA en bourse ?
[29] European Investment Bank, “European Cybersecurity Investment Platform,” 2022, https://www.eib.org/en/publications/20220206-european-cybersecurity-investment-platform. (accessed on November 8, 2024).
[30] Kunzel, P., Lu, Y. and Petrova, I., “Investment Objectives of Sovereign Wealth Funds—A Shifting Paradigm,” International Monetary Fund Working Paper, WP 11/19 (2011).









